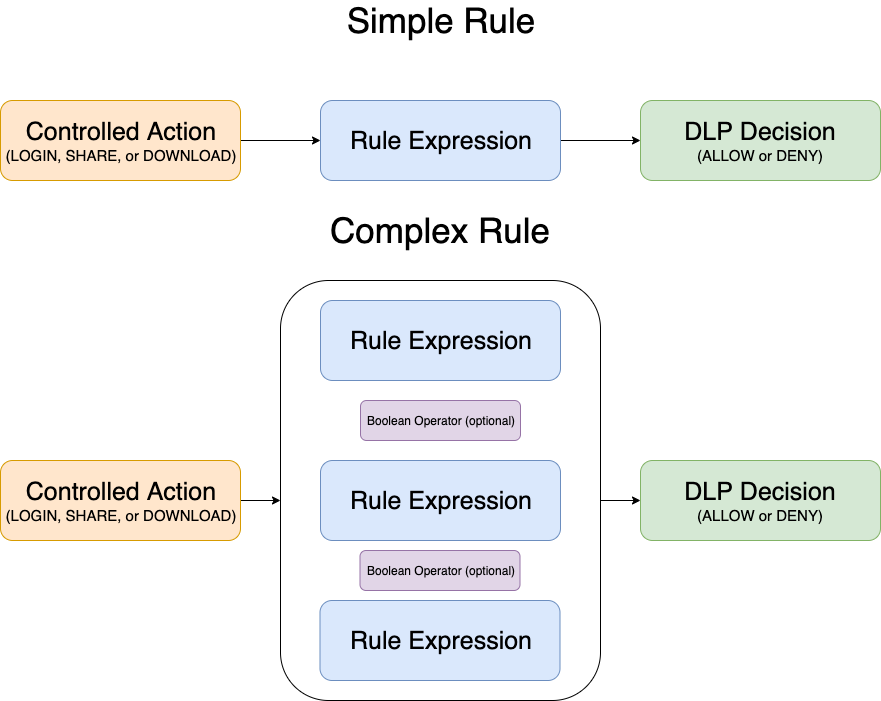
Rule Expressions
Rule Expressions are the parameters by which DLP policies determine a user or group's ability to login into the FileCloud system, as well as to download or share files. Rule Expressions also enable administrators to access detailed information about user activity on their FileCloud installations.
Logical operators
DLP permits users to implement two or more rules using the logical operators '&&' , '||', and '!'.
Learn more about logical operators.
DLP Rule Expressions
| Expression | What does the expression do? | Sample returned value | Applicable actions |
|---|---|---|---|
| _request.remoteIp | Returns the IP address that was used to execute the action. | _request.remoteIp == '43.12.45.78' | DOWNLOAD, LOGIN |
| _request.isAdminLogin | Returns true for admin login request. | _request.isAdminLogin | LOGIN |
| _request.agent | Returns the user agent that was used to execute the action. The possible values are: 'Cloud Drive', 'Cloud Sync', 'Unknown', 'Web browser', 'Android', 'iOS', 'MS Outlook' and 'MS Office'. | _request.agent == 'Unknown' | DOWNLOAD, LOGIN |
| _request.inIpv4Range(lowIp, highIp) | Checks if the IP address that was used to execute the action is part of a given IP range, represented by limits of the range (given with the parameters). | _request.inIpv4Range('138.204.26.254', '138.204.26.1') | DOWNLOAD, LOGIN |
| _request.remoteCountryCode | Returns the two-character uppercase ISO country code. Returns "Unknown" if country could not be determined. Note: To use this expression, the Show Geo IP Chart setting in the Settings > Admin screen must be set to TRUE. | _request.remoteCountryCode == 'US' | DOWNLOAD, LOGIN |
| _request.inIpV4CidrRange(cidrRange) | Checks if the IP address used to execute the action matches the given CIDR range. | _request.inIpV4CidrRange('10.2.0.0/16') | DOWNLOAD, LOGIN |
| _user.username | Returns the name of the user trying to execute an action. Note: This cannot be used to identify the master Admin since "admin" is not stored as a user. Instead use user.isMasterAdmin (see below). | _user.username == 'FileCloudUser' | DOWNLOAD, LOGIN, SHARE |
| _user.email | Returns the email of the user trying to execute an action. | _user.email == 'john.doe@mail.com' | DOWNLOAD, LOGIN, SHARE |
| _user.userType | Returns the type of user that is trying to execute the action. The available types are: 'Full Access', 'Limited Access', 'Guest Access'. Note: Prior to FileCloud 22.1, the three user types were Full, Limited, and Guest. Beginning in FileCloud 22.1 Limited users are referred to as External users; however, the DLP rule expression still requires the use of the value 'Limited Access' to refer to these users. | _user.userType == 'Guest Access' | DOWNLOAD, LOGIN, SHARE |
| _user.inGroup(groupName) | Checks if a user is part of a given group. | !_user.inGroup('managers') | DOWNLOAD, LOGIN, SHARE |
| user.isEmailInDomain(domainsToCheck) | Checks if a user's email id matches a given list of domains. The 'domainsToCheck' parameter can be a single domain, or a comma-separated domains list. | _user.isEmailInDomain('example.com', 'mail.com') | SHARE |
| user.isMasterAdmin | Checks if user is the master Admin. Note: _user.username =='admin' cannot be used in place of this to identify the master Admin since "admin" is not stored as a user. | user.isMasterAdmin | DOWNLOAD, LOGIN, SHARE |
| _file.path | Returns the path that was accessed. | _file.path == '/myuser/mydir/myfile.pdf' | DOWNLOAD |
| _file.pathStartsWith(start) | Returns true when the path has been accessed. Starts with the given `start` parameter. | _file.pathStartsWith('/myuser/mydir') | DOWNLOAD |
_file.ext | Checks if the file has the extension specified. | _file.ext == 'pdf' | DOWNLOAD |
_file.pathContains(path) | Checks if the file path contains the sub-path specified. | _file.pathContains('/myuser/mydir') | DOWNLOAD |
_file.pathMatches(path) | Checks if the file path matches the path specified. | _file.pathMatches('/myuser/mydir') | DOWNLOAD |
| _file.fileNameContains(text) | Checks if the filename includes the given text. | _file.fileNameContains('mrn') | DOWNLOAD |
| Note: When you set a _metadata rule, the metadata set and the attribute specified cannot contain periods within their names. For example, cce.pii is valid, but cce.x.pii.y is not valid. | |||
| _metadata.exists(metadataValue) | Checks if the path or one of its children, have the given metadata attribute set. The metadata attribute must be provided using the `metadataSet.attribute` notation. | _metadata.exists('cce.pii') | DOWNLOAD, SHARE |
| _metadata.existsAll(metadataValue) | Checks if the path or all of its children, have the given metadata attribute set. The metadata attribute must be provided using the `metadataSet.attribute` notation. | _metadata.existsAll('cce.pii') | DOWNLOAD, SHARE |
| _metadata.existsWithValue(metadataValue, value) | This function is similar to the _metadata.exists(metadataValue) function, but it checks if the metadata attribute (first parameter) exists, and if its value is equal to a given value (second parameter). | _metadata.existsWithValue('content.category', 'confidential') | DOWNLOAD, SHARE |
| _metadata.existsWithValueInArray(metadataValue, value) | This function is similar to the `_metadata.existsWithValue(metadataValue, value) function, but checks whether an array metadata attribute contains the specified value. | _metadata.existsWithValueInArray('content.categories', 'pii') | DOWNLOAD, SHARE |
| _metadata.existsWithCondition(metadataValue, operator, value) | This function is similar to the _metadata.existsWithValue(metadataValue, value) function, but it takes an operator parameter (second parameter) that will be used to compare the metadata attribute value (first parameter) with the provided value (third parameter). The available operators are: `==` (equals), `!=` or `<>` (not equal), `>` (greater than), `<` (less than), `>=` and `<=`. When the metadata and the third operator are numbers, they'll be compared as numbers. If any parameter is not a number, it will be compared alphabetically (dates, for example, cannot be compared using `>, <, >=, <=`). The sample checks if the risk level of a document is greater than 6. | _metadata.existsWithCondition('content.Risk Level', '>', 6) | DOWNLOAD, SHARE |
| _share.path | Returns the path of the share. | _share.path == '/myuser/mydir/myfile.pdf' | SHARE |
| _share.public | Returns true or false if the share is public or not. | _share.public | SHARE |
| _share.onlyAllowedEmails | Checks if all users receiving a share match one of the emails or one of the domains specified in the rule. A domain may be specified instead of an email by using *, for example *@gmail.com. If any recipients do not match an email or domain specified, the share is denied. | 'true' if all share recipients are in a domain or email in the onlyAllowedEmails list. 'false' if any share recipient is not in any of the domains or emails in the onlyAllowedEmails list. | SHARE |
| _share.allowedUsers | Returns a list of the allowed users of the share (including the users in an allowed group). The list contains the users' email addresses. | 'john.snow@mail.com' in _share.allowedUsers | SHARE |
| _share.allowedGroups | Returns a list of the allowed groups of the share. | 'EVERYONE' in _share.allowedGroups | SHARE |
| _share.hasUsersFromDomain(domain) | Checks if the allowed users list has any users with an email domain that matches the given domain. In the provided sample, the expression will return true if any user with a gmail domain is included as an allowed user (directly or through a group). This method only makes sense with DENY rules. | _share.hasUsersFromDomain('gmail.com') | SHARE |
| _share.onlyUsersFromDomain(domain) | Similar to the _share.hasUsersFromDomain(domain) function, but checks if the allowed users list has any user with an email domain that doesn't match the given domain. In the provided sample, the expression only returns true if all users have their emails in the `mycompany.com` domain. This method only makes sense with ALLOW rules. Do not use this expression in an OR condition with another expression; this could cause shares to be denied unintentionally. Instead use _share.onlyAllowedEmails with a wildcard. _share.onlyAllowedEmails('*@gmail.com','testuser@test.com') | _share.onlyUsersFromDomain('mycompany.com') | SHARE |
| _share.pathStartsWith(start) | Returns true when the shared path starts with the given `start` parameter. | _share.pathStartsWith('/myuser/mydir') | SHARE |
| _share.pathContains(text) | Returns true when the shared path contains the given `text` parameter. | _share.pathContains('sometext') | SHARE |
| _share.pathMatches(pattern) | Returns true when the shared path matches the given `pattern` parameter. Wildcards are supported: `*` for any sequence of characters and `#` for a single character. | _share.pathMatches('*sometext*') | SHARE |
Logical Operators
DLP allows users to implement logical operators to further refine and specify their data leak prevention rules.
Logical Operator Examples
| Applicable Action | DLP Ruling | Rule Expressions | Result |
|---|---|---|---|
| DOWNLOAD | DENY | _user.username == 'john' && _user.inGroup('engineers') | User 'john' in group 'engineers' will not be permitted to download any files. |
| DOWNLOAD | ALLOW | _user.inGroup('accounting') || _request.remoteIp == '69.89.31.226.' | Users in group 'accounting' or users from the listed IP will be permitted to download files, but no other users will be permitted. |
| SHARE | DENY | !_user.inGroup('designers') | Users who are not a member of group 'designers' will not be permitted to share files. |