SIEM Integration
Security information and event management (SIEM) products and services provide analysis of security alerts generated by applications and network hardware.
FileCloud can integrate its system alerts and auditing with external SIEM systems, enabling you to monitor all alerts and potential security issues in one place.
Open the SIEM settings page
Set up SIEM
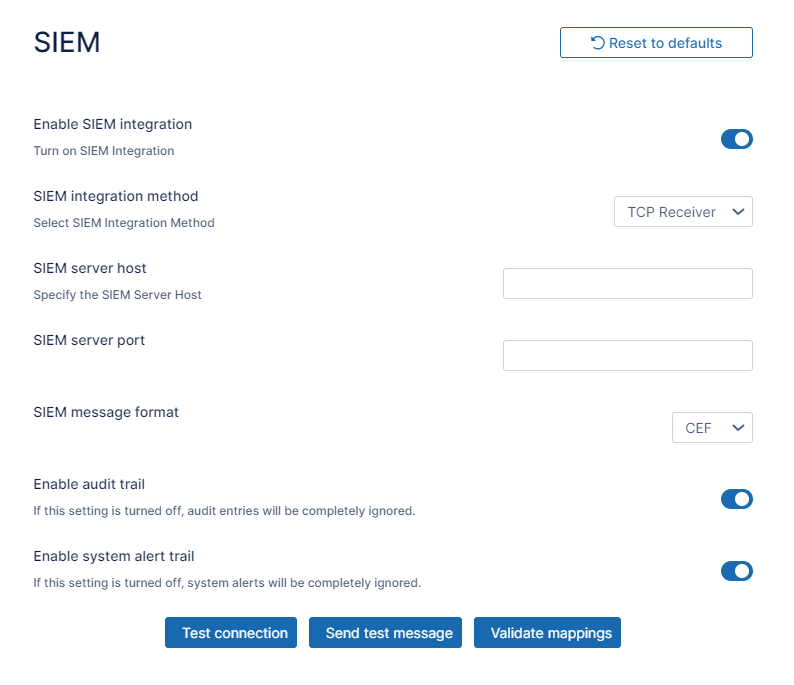
- To activate SIEM integration, click the grayed out Enable SIEM integration button.
SIEM integration fields appear. - Modify the settings using the information in the following table.
Option Description SIEM integration method Specifies the SIEM Integration method. Following options are available:
- TCP Receiver - messages are sent to the specified SIEM server endpoint (host and port) via TCP socket connection
- UDP Receiver - messages are sent to the specified SIEM server endpoint (host and port) via UDP socket connection
- Syslog - messages are written directly to the Syslog, which can be imported by the SIEM server
Note: SIEM software providers should specify supported integration methods in the SIEM documentation.
SIEM server host (TCP and UDP integration only) URL or IP Address of the SIEM server. SIEM server port (TCP and UDP integration only) Port exposed by the SIEM Server for the given socket connection. SIEM message format Specifies the SIEM Message format. The following formats are available:
- CEF - Common Event Format
- LEEF - Log Event Extended Format.
NOTE: SIEM software provider should specify supported formats in the SIEM documentation.
LEEF version (LEEF Format only) Specifies the version of the LEEF format message. Available versions:
- 1.0
- 2.0
LEEF message delimiter (LEEF Format only) The delimiter to be used for LEEF messages. The options are whitespace and tab. Choose the option that is compatible with the SIEM tool you are using. Enable audit trail Specifies whether Audit records should be processed and send to the SIEM Server. Please check the Managing SIEM mappings section for more details.
Enable system alert trail
Specifies whether System Alerts generated within FileCloud should be processed and send to the SIEM Server. Please check the Managing SIEM mappings section for more details. Test connection (TCP and UDP integration only) Tests connection to the server specified by the Host and Port.
NOTE: All settings have to be saved first. Connection tests are based on the currently saved settings.
Send test message Sends a test message in the given format (CEF/LEEF) to the SIEM server specified by the Host and Port or saves a test message to the Syslog.
NOTE: All settings have to be saved first. Connection tests are based on the currently saved settings.
Validate mappings Validates all defined mappings. Please check the Managing SIEM mappings section for more details. - Click Save.
Syslog Integration
In order to provide more flexibility, FileCloud allows admins to specify two important Syslog parameters - ident and facility. Ident specifies the name of the application logged in Syslog. Facility specifies where all FileCloud messages are sent and can be utilized by the system level Syslog configuration (e.g. in "rsyslog"). Both settings can be overridden in the cloudconfig.php configuration file by inputting the following settings:
Ident - to specify ident value, add the following setting to cloudconfig.php
define('TONIDOCLOUD_SIEM_SYSLOG_IDENT', 'IDENT_VALUE');If no value is provided, by default it will be set to 'SIEM'.
Facility -to specify ident value please add the following setting: to the cloudconfig.php
define('TONIDOCLOUD_SIEM_SYSLOG_FACILITY', LOG_LOCAL2);If no value is provided, by default it will be set to LOG_LOCAL5. Below is a full list of supported values.
LOG_AUTHSecurity/authorization messages (use LOG_AUTHPRIVinstead in systems where that constant is defined)LOG_AUTHPRIVSecurity/authorization messages (private) LOG_CRONClock daemon (cron and at) LOG_DAEMONOther system daemons LOG_KERNKernel messages LOG_LOCAL0...LOG_LOCAL7Reserved for local use. These are not available in Windows LOG_LPRLine printer subsystem LOG_MAILMail subsystem LOG_NEWSUSENET news subsystem LOG_SYSLOGMessages generated internally by syslogd LOG_USERGeneric user-level messages LOG_UUCPUUCP subsystem LOG Values can also be seen in the official PHP documentation.
Please note that there are no quotation marks used for LOG values, as these have to be set to one of the PHP constants.
Managing SIEM Mappings
The biggest challenge when working with the external SIEM servers is to map messages existing in the system to the correct CEF/LEEF format. In order to allow administrators to have full control of how to represent FileCloud's system alerts and audit records in the external SIEM system a special, flexible mapping syntax is supported.