LDAP Based Authentication
In this mechanism, a user account is authenticated against an external LDAP server.
Accounts with this type of authentication are also known as external accounts.
By default, LDAP communications between client and server applications are not encrypted.
- This means that it could be possible to use a network monitoring device or software to view the communications traveling between LDAP client and server computers.
- This is especially problematic when an LDAP simple bind is used because credentials (username and password) are passed over the network unencrypted. This could quickly lead to the compromise of credentials.
Therefore, it is recommended that you enable Lightweight Directory Access Protocol (LDAP) over Secure Sockets Layer (SSL) or Transport Layer Security (TLS).
- SSL and TLS are also known as LDAPS
- Some applications authenticate with Active Directory Domain Services (AD DS) through simple BIND. If simple BIND is necessary, using SSL/TLS to encrypt the authentication session is strongly recommended.
- Use of proxy binding or password change over LDAP requires LDAPS. (e.g. Bind to an AD LDS Instance Through a Proxy Object )
- Some applications that integrate with LDAP servers (such as Active Directory or Active Directory Domain Controllers) require encrypted communications.
Prerequisites
The LDAP service must be accessible from FileCloud (IP and Port must be accessible).
LDAP must support Simple Authentication Method (Anonymous or Name/Password Authentication Mechanism of Simple Bind).
LDAP users must have an email attribute.
- If LDAP Authentication is enabled, then Automatic User creation cannot be enabled (i.e, All user creation should be done in LDAP server)
- The LDAP user will count towards FileCloud License only after the user account logs into FileCloud
Enable LDAP Authentication
To enable LDAP Authentication in FileCloud:
- In the FileCloud admin portal's left navigation bar, scroll down and click Settings. Then, on the Settings navigation page, click Authentication .
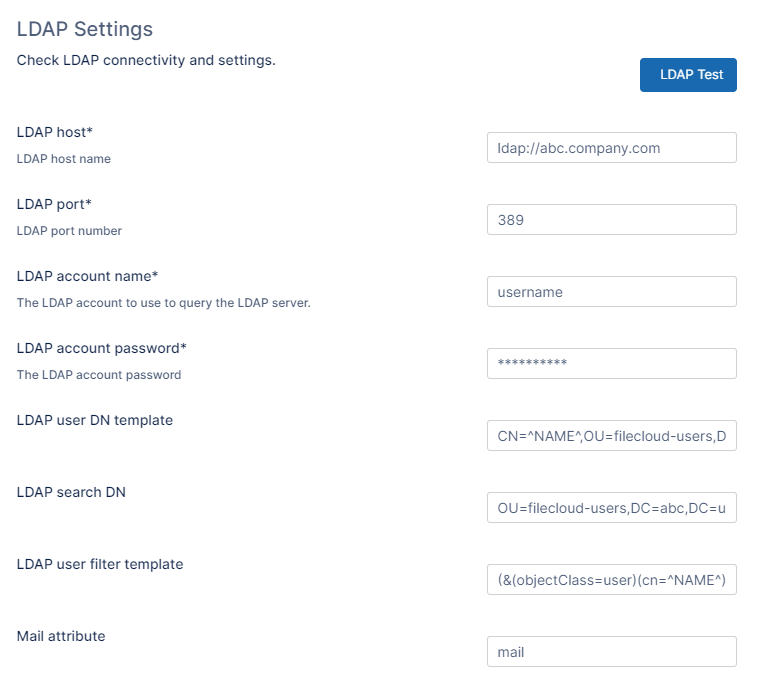
The Authentication page opens. Under Authentication Settings, in Authentication Type select LDAP.
In LDAP Settings, enter the required information, and then click Save.
If you are using multiple LDAP servers, see Authenticate to Multiple LDAP Servers.