ADFS Single Sign-On Support
Introduction
FileCloud offers a SAML-based Single Sign-On (SSO) service that provides customers with full control over the authorization and authentication of hosted user accounts.
Using the SAML model, FileCloud acts as the service provider and also a claims-aware application. FileCloud customers that host FileCloud can authenticate against Active Directory Federation Services (ADFS) and log in to FileCloud.
FileCloud acts as a Service Provider (SP) while the ADFS server acts as the identity provider (IdP).
Active Directory Federation Services (ADFS) Support
When SAML SSO Type is selected and ADFS is enabled in FileCloud, FileCloud accepts claims in the form of ADFS security tokens from the Federation Service, and can use ADFS claims to support Single Sign-On (SSO) into FileCloud.
To specify the identity claims that are sent to the FileCloud refer to the IdP Configuration section below.
Prerequisites
- A Working ADFS implementation. This is beyond the scope of FileCloud. Please refer to articles available on the internet on setting up ADFS.
FileCloud must be running on HTTPS using SSL. (Default self-signed SSLs that ship with FileCloud do not work). ADFS does not allow adding a relying party that is running on HTTP or self-signed SSL. For help setting up SSL in FileCloud, see set up SSL in FileCloud.
FileCloud SSO Configuration Steps
In order to successfully configure SSO:
- Configure Apache Webserver.
- Set SAML as a the default single sign-on method in FileCloud and configure IdP settings.
- Enable single sign-on link on the login page.
- Register FileCloud as a service provider (SP) with IdP by adding FileCloud as a Relying Party Trust in ADFS.
Step 1: Apache Web Server Configuration
Follow the steps in SAML Single Sign-On Support to set up the Web Server configuration and enable SSO.
Step 2: Set SAML as the default SSO method and configure IdP/ADFS
- In the FileCloud admin portal's left navigation bar, scroll down and click Settings. Then, on the Settings navigation page, click SSO .
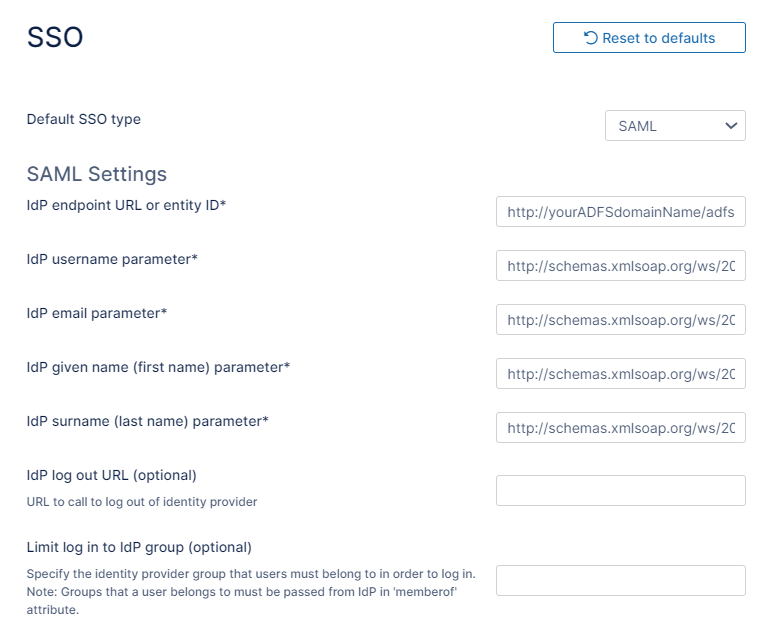
The SSO page opens. - Set Default SSO Type to SAML.
- Set the other fields as specified in the following table.
| FileCloud Parameters | ADFS as IdP Data can be obtained from Federation Metadata | |
|---|---|---|
Default SSO Type | For ADFS, select SAML | |
IdP End Point URL | Identity Provider URL (Entity ID) e.g. http://yourADFSdomainName/adfs/services/trust | |
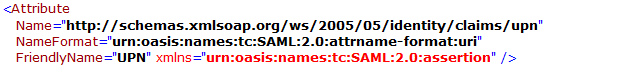
IdP Username Parameter | Identifies the Username (must be unique for each user) value: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn or upn | |
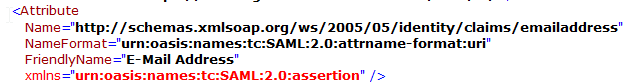
IdP Email Parameter | Identifies the email of the user (must be unique) http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress or emailaddress | |
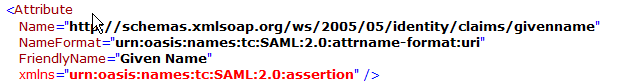
IdP Given Name Parameter | Identifies the given name of the user. http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname or givenname | |
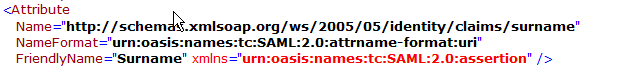
IdP Surname Parameter | Identifies the surname of the user http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname or surname | |
| IdP Log Out URL (Optional) | URL for logging out of IdP Note: For this setting to be effective, you must also add a setting to the FileCloud config file:
| |
| Limit Logon to IdP Group (Optional) | IdP Group Name
| |
IdP Metadata | ||
SSO Error Message (Optional) | Custom error message that appears when a signin is invalid. Enter in HTML format. | |
| Allow Account Signups Added in FileCloud 20.1 | When TRUE, during the login process, if the user account does not exist, a new FileCloud user account is created automatically. | |
Automatic Account Approval Added in FileCloud 20.1
| This setting works with the Allow Account Signups setting to determine:
See Integrating Multiple IDPs for help configuring multiple IDPs with automatic account approval settings specific to each one. | |
| Enable ADFS | Yes | |
| User login token expiration match Idp expiration | If enabled the user token expiration will be set based on ADFS expiration settings If not enabled user token expiration will be set based on FileCloud Session Timeout Default: No (Not enabled) | |
Enable Browser-Only SSO Session Timeout | If enabled, SSO session timeouts apply to browser sessions but not to client sessions. | |
| Show the IdP Login Screen | If enabled, automatically redirect user to IdP log-in screen. | |
| Log Level | Set the Log level for SAML calls. Default Value: PROD (Do not use DEV for production systems) |
Step 3: Enable SSO link on the login page
Follow the steps in SAML Single Sign-On Support (under SSO Configuration Steps, Step 6) to enable SSO sign-in on the user portal or admin portal.
Step 4: Register FileCloud as SP in IdP/ADFS
Registering FileCloud as SP in ADFS involves series of steps from adding FileCloud as a Relying Party Trust in ADFS to setting up Claim Rules for FileCloud in ADFS. Please follow the steps below to successfully register FileCloud in ADFS.
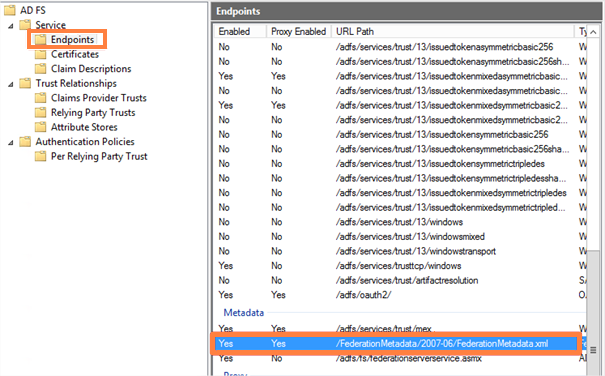
Before you proceed, you must be able to download the metadata of FileCloud from the following Entity ID URL. (Note HTTPS).
https://<Your Domain>/simplesaml/module.php/saml/sp/metadata.php/default-sp
If you have trouble downloading the metadata from the above URL, please check if HTTPS is working and Steps 1, 2 and 3 above were completed successfully.
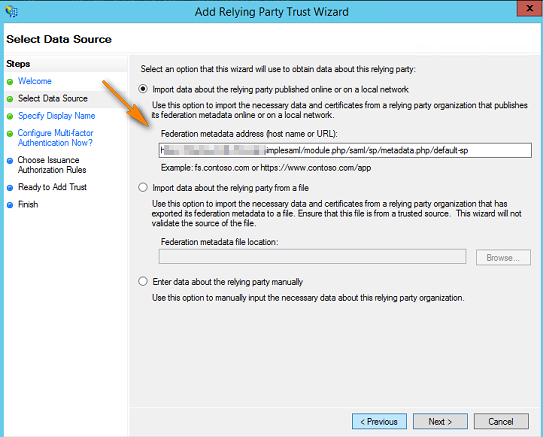
- On your ADFS server, open the ADFS management console, expand Trust Relationships and select the Relying Party Trust node. In the Actions pane, click Add Relying Party Trust.
- Click Start, then paste the Entity ID URL from above into the Federation Metadata address field and click Next.
Note: You can do this manually by downloading your metadata file from http://<your domain>/simplesaml/module.php/saml/sp/metadata.php/default-sp and importing it into ADFS by choosing Import data about the relying party from a file.Once you access the metadata URL you need to enter admin credentials to be able to download the metadata file. The username is admin and the password can be found in:
<FileCloud WEB ROOT>/thirdparty/simplesaml/config/config.php - Accept the warning
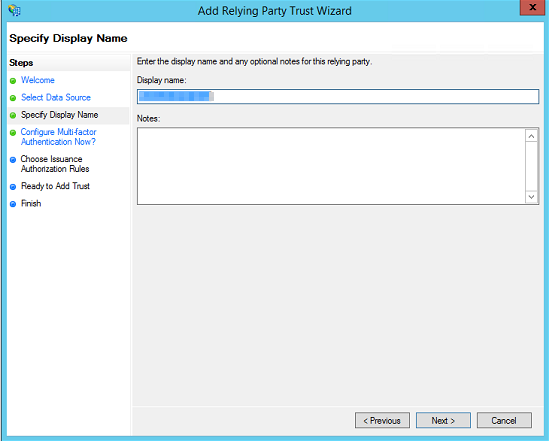
- Enter the display name for the Relying Party Trust, usually your FileCloud URL.
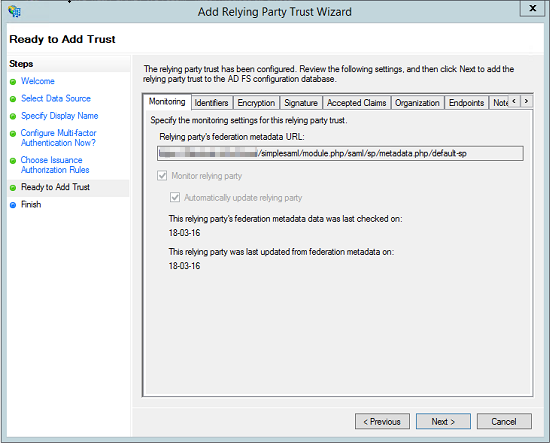
- Click Next several times in the wizard until you reach the Ready to Add Trust page. Here, review the tabs. The Encryption and Signature tabs must have values associated with them.
- Click Next. The new Relying Party Trust is now added.
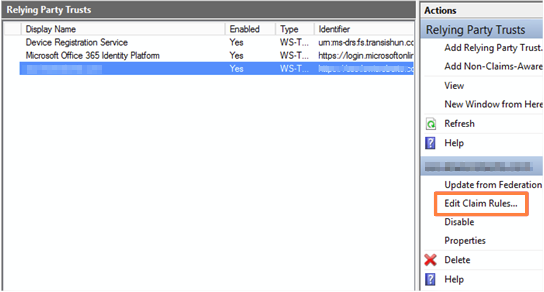
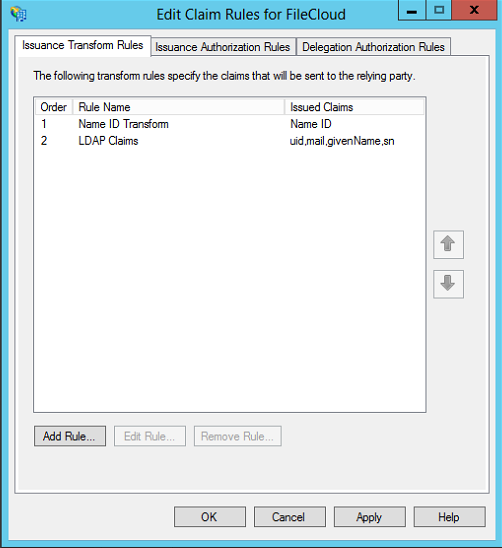
- Select the Relying Party Trust we have just added and then click Edit Claim Rules.
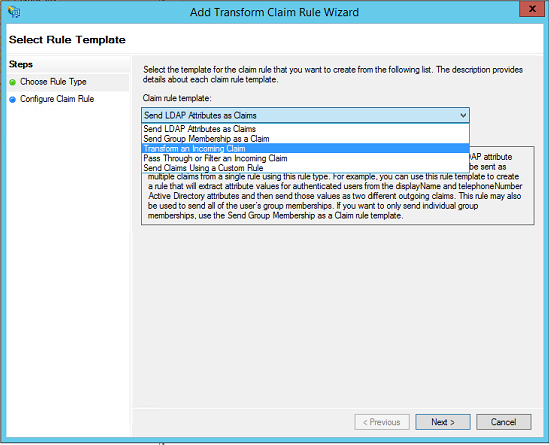
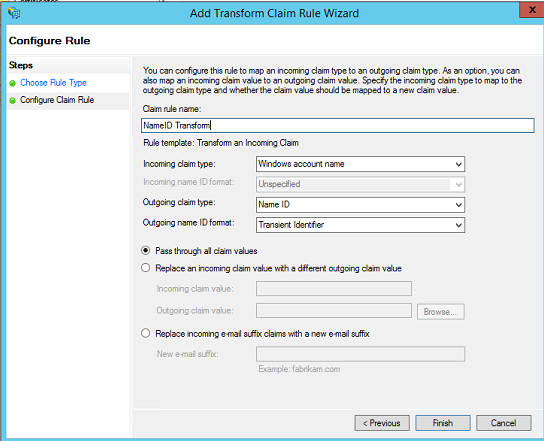
- Add an Issuance Transform Rule. Choose the Transform an Incoming Claim rule template.
- Give a Claim rule name (Name ID Transform - can be anything). Choose Windows account name as Incoming claim type and Name ID as Outgoing claim type. Choose Transient Identifier for Outgoing name ID format. Select the radio button Pass through all claim values. Click Finish to add the claim rule.
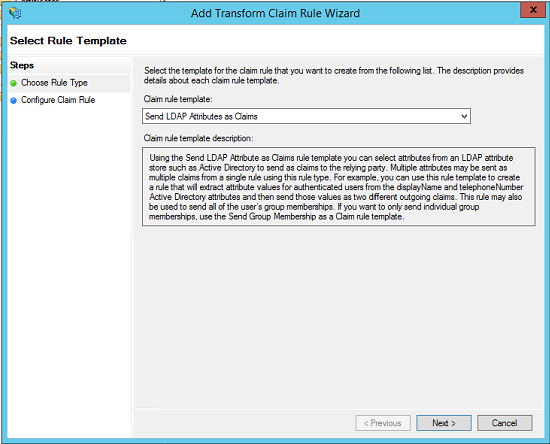
- Add another issuance transform rule. Select Send LDAP Attributes as Claims template.
- Fill in the rule fields:
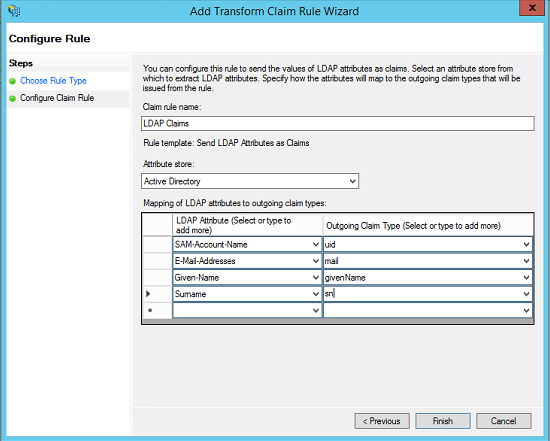
- Enter a Claim rule name (LDAP Claims - can be anything).
- Select Active Directory as Attribute store.
- Enter the mapping values of LDAP Attributes to Outgoing Claim Types. The outgoing claim type must match the names as specified in FileCloud SSO Settings UI Page (the screenshot below follows the FileCloud SSO Settings as documented above).
- For Outgoing Claim Type, uid and mail are required. SAM-Account-Name in the screenshot below can be replaced with UPN if desired.
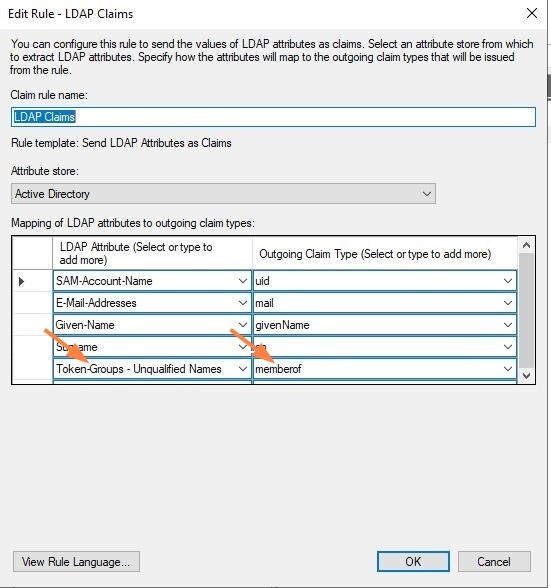
- For ADFS configuration, add an additional claim parameter (Token-Groups - Unqualified Names > memberof).
- Click Finish to add the rule.
- Once configured, you should have two issuance transform rules (Name ID Transform and LDAP Claims if you followed the steps above). Click Apply and Exit.
This completes the ADFS configuration and FileCloud is added as a Relying Party Trust in the ADFS server. You can now test SSO from FileCloud by going to the FileCloud login page and clicking the Single Sign-On link as mentioned in Step 3, above.
Troubleshooting
Please check the troubleshooting section from SAML Single Sign-On Support.