Setting up FileCloud Managed Azure Blob Storage
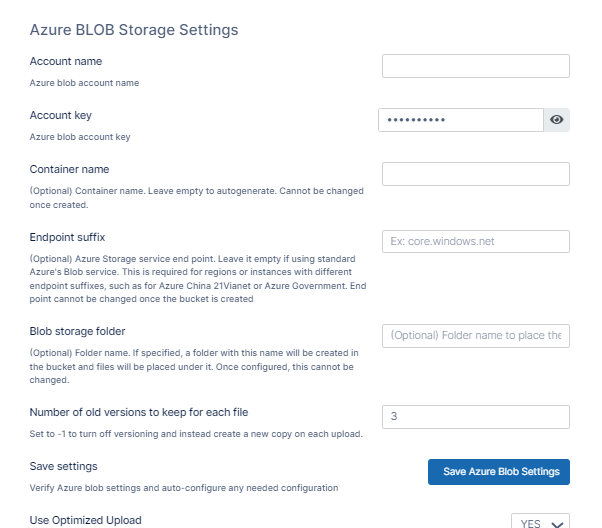
As an administrator, you can integrate FileCloud Server to store user data on an Azure Blob storage server.
|
|---|
Getting Started with Azure Blob Storage
WARNINGS:
- Only change the FileCloud storage type to Blob for new installations.
- Do not change the FileCloud storage type to Blob if FileCloud has been in use and data is already stored.
- Be very careful when changing the storage path. If done improperly, it could lead to data loss.
- When changing the storage type from local to Azure Blob, the files and folders that have already been saved to local storage will not be moved automatically to Blob storage.
- For existing files and folders, the administrator must manually export them from local storage before changing the storage type.
- After changing the storage type to Blob, the administrator must manually import pre-existing files and folders.
- The Azure Storage Container should NEVER be modified outside of the FileCloud subsystem.
- Do not add/edit/modify files directly using Azure Storage tools. Doing so will destabilize your FileCloud installation.