
Info: This is the second post in the series “Smart Classification, Metadata, and Smart DLP – the powerful combo” about data classification and security in FileCloud.
In the previous post, we explained the concepts and capabilities of File Cloud’s metadata subsystem, which allows users to describe data available in their system by assigning extensive sets of information to them. As we’ve shown, metadata can be used to search for particular files or to grant or decline operations like download or share via the Smart DLP subsystem. In this post we’ll discuss that particular subsystem alone, explaining how it works, and what protection it can give in real-world scenarios.
Smart DLP
DLP stands for Data Leak Prevention, which, simply put, protects your data from “leaking” by enforcing sets of rules on how data can be manipulated and retrieved. In FileCloud this can be achieved by creating rules in the Smart DLP subsystem. During program execution, these rules are evaluated and particular operations are allowed or blocked. Let’s dive a little bit deeper into what is possible in FileCloud, version 20.3.
When admins visit the Smart DLP screen, they see a list of all available DLP rules with details about each of them.
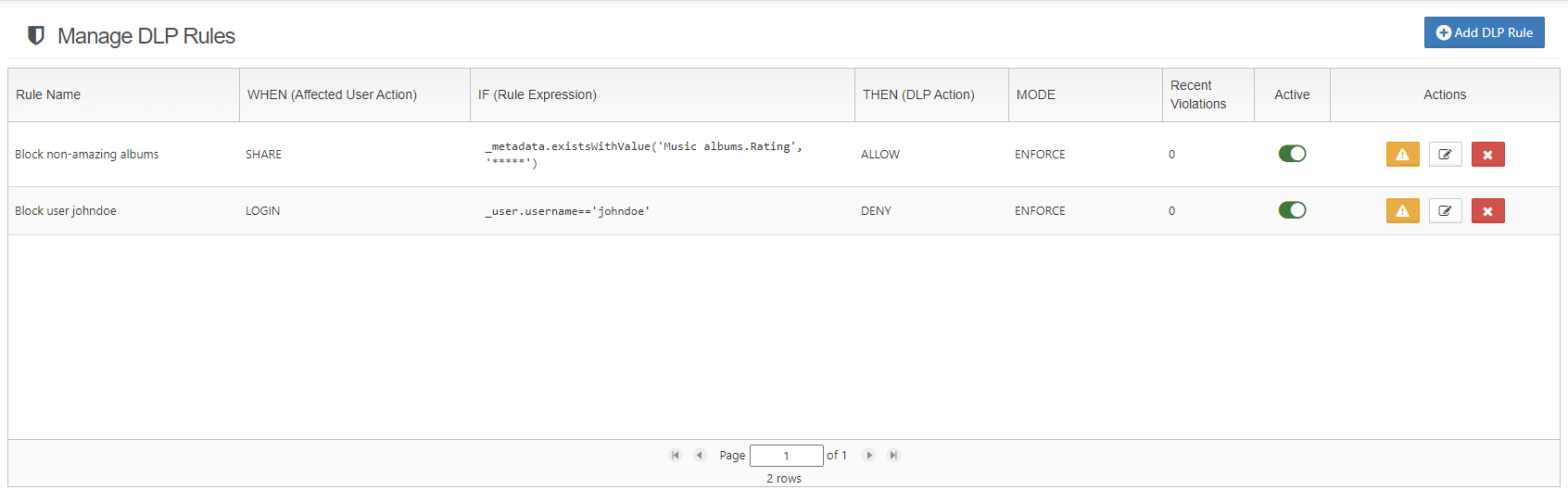
DLP rule definition is very powerful, allowing admins to really narrow use cases by specifying user actions, mode, the rule expression, the DLP action and mode, and notifications. Let’s explain each area in more detail.
Affected User Actions
This property allows admins to specify which actions performed by users will be monitored and protected by the given DLP rule. FileCloud version 20.3 provides support for download, share and login operations.
Rule Expression
This is the heart of the DLP rule, and allows admins to specify the actual use case they want to prevent or monitor. The rule expression engine in File Cloud’s Smart DLP is very flexible and allows combining multiple conditions into a single rule. We’ll discuss available options in more details later.
DLP Action
Provides two possible actions: DENY and ALLOW, which specify what should happen if the rule expression is matched. Based on that setting, the same rule can be used to either grant or prohibit a login or a download operation for the given user.
DLP Mode
This property takes one of two available values, Enforce or Permissive, that specify how the system behaves when the rule is met. When the rule works in Enforce mode, it blocks any rule violation attempts.. For example, a 403 status is returned by the API if a user without permission tries to download a file, or a share operation is blocked if a user tries to share a protected file or tries to share it with non-permitted users. In addition, the violation attempt is logged. On the other hand, Permissive mode performs logging and monitoring of violation attempts without blocking the actual operation. This allows admins to monitor and trace some potentially insecure patterns without enforcing policies that might be too restrictive.
Rule Notification
Allows admins to provide custom messages that are displayed if a rule is violated. This is applicable only to the Download and Share actions.
Rule Expressions
FileCloud provides multiple predefined expressions that can be used as building blocks when creating more complex DLP rules. An important note is that the set of available predefined expressions depends on the user action the admin wants to allow or deny. The reason for that is simple – the required data for some of the flows may not be present. For example, when a user tries to log in we might not have any information apart from the request details and user’s email or username, so we cannot use an expression that requires additional data. On the other hand, when protecting a download operation, additional information about the file being processed is present, so more expressions are available for use. Let’s briefly review lists of available expressions grouped by the data they operate on.
Request related
- remoteIp – returns the IP address that has been used to execute the action, for example, 43.12.34.123
- agent – returns the user agent that has been used to execute the action
- inIpv4Range(low, high) – checks whether the IP address used to perform the action is a part of the given range
- remoteCountryCode – Returns the two character, uppercase ISO code of the country, for example, ‘US’
- inIpV4CdirRange(cdir) – Checks whether the IP address used to execute the action matches the given CDIR range, for example, ’10.2.1.0/24’
User related
- username – returns the username of the user trying to execute the action
- email – returns the email of the user trying to execute the action
- userType – Returns the type of the user trying to execute an action. Available types are: ‘Full Access’, ‘Limited Access’, ‘Guest Access’
- inGroup(groupName) – Checks if a user is a member of a given group
- isEmailInDomain(domains) – Checks if a user’s email matches any of the given, comma separated domains, for example, _user.inGroup(‘email.com,email.net’) will return true for the following emails: accounts@email.com, johndoe@email.net.
File related
- path – returns the path of the file being downloaded
- pathStartsWith(path) – checks whether the file’s path starts with the given string
Metadata related
- exists(metadata) – checks whether the file (or any of the files if a folder is downloaded) has the given metadata attribute assigned
- existsWithValue(metadata, value) – Similar to the previous expression, but checks for a specific value in the metadata attribute.
- existsWithCondition(metadata, operator, value) – Checks whether the value exists and matches the expression. The following operators are supported: == (equals), != or <> (not equal), > (greater than), < (less than), >=, (greater than or equal to) <= (less than or equal to). For example, metadata.existsWithCondition(‘secure.risk_level’, ‘>’, 3) will return true when any of the files being downloaded contains the secure.risk_level attribute with a value greater than 3.
Share related
- path – returns the path of the share location
- public – checks whether the share is public or not
- _share.allowedUsers – returns a list of emails of users allowed to access the share
- allowedGroups – returns a list of groups allowed to access the share
- hasUsersFromDomain(domain) – Checks if the allowed users list has any user whose email MATCHES any of the domains provided in the domain comma-separated list. This method is only applicable for the DENY rule
- onlyUsersFromDomain(domain) – Checks if the allowed users list has any user whose email DOESN’T MATCH any of the domains provided in the domain comma-separated list. This method is only applicable for the ALLOW rule
- pathStartsWith(path) – returns true if the share location starts with the given path
- pathContains(text) – returns true if the share path contains the given ‘text’
- pathMatches(pattern) – returns true if the path matches the given pattern. This expression uses simplified regex syntax, allowing wildcards ‘*’ and single characters ‘#’
As mentioned earlier, FileCloud’s Smart DLP supports three operations – login, download and share. The following groups of expressions are supported for each one:
Download – request, user, file, metadata
Share – user, metadata, share
Login – request, user
Rule expressions can be combined with each other with logical operators, which makes Smart DLP a very powerful tool. The diagrams below explain how DLP operates.
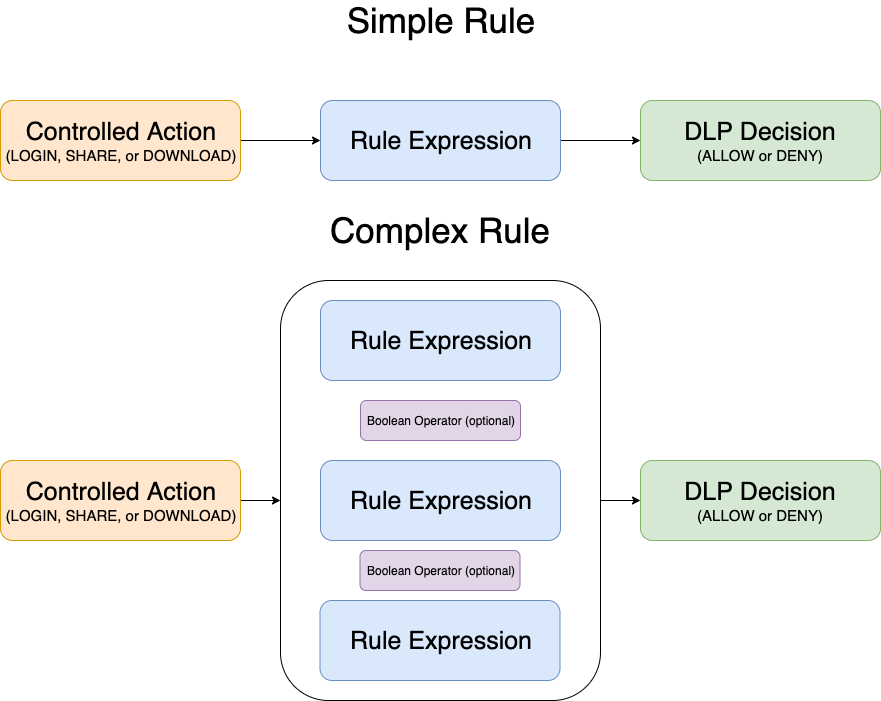
Source here.
The following algorithm is used when evaluating the action:
- Check if the controlled action (Login, Share, Download) is being performed.
- If yes find ALL DLP rules matching that action.
- For each DLP rule that matches, evaluate the specified rule expression (simple or complex)
- If the rule expression returns true decide whether access is granted or denied based on the ALLOW/DENY parameters. DENY behavior varies depending on whether the rule is enforcing or permissive. The former will break the chain of checks and block the action, and the latter will grant access for the given DLP rule, log the violation and continue with the next rule.
Common Use Cases
Equipped with knowledge about the basic building blocks, we can start exploring some interesting possibilities that they provide when we start combining them.
- Prevent login from outside the given country
This scenario is pretty common since it is a part of many compliance policies (for example, ITAR). It can be achieved with the given rule:
| Affected action |
DLP Action |
Rule expression |
| LOGIN |
DENY |
_request.remoteCountryCode != ‘US’ |
Note: As with almost all DLP rules this can be achieved alternately by negating the condition in the expression and changing the DLP Action to ALLOW. The new rule would ALLOW access if the country code equals `US`, whereas the original one says – DENY access from outside of the US.
Note: The country code feature requires GeoIP service synchronization, which allows mapping IPs to the country code.
- Limit login to users from the company’s domain via web browser only
This scenario allows login only for users whose emails match the company’s domain and only for the web browser client.
| Affected action |
DLP Action |
Rule expression |
| LOGIN |
DENY |
_user.isEmailInDomain(‘company.com’) and _request.agent == ‘Web browser’ |
- Prevent sharing of internal files to external users
This scenario prevents public sharing and private sharing to users that are not members of the Company group if documents are marked as internal (which can be done automatically with File Cloud’s Smart Classification subsystem).
| Affected action |
DLP Action |
Rule expression |
| SHARE |
ALLOW |
_metadata.existsWithValue(‘Security.internal’, false) or (_metadata.existsWithValue(‘Security.internal’, true) and _user.inGroup(‘CodeLathe’)) |
- List of allowed IPs for external downloads
This scenario prevents downloads for users who are not a part of the internal user group unless the download is performed from the user’s office location (known IP address).
| Affected action |
DLP Action |
Rule expression |
| DOWNLOAD |
ALLOW |
_user.inGroup(‘Internal’) or (_user.inGroup(‘Trusted Company’) and _request.remoteIp == ’13.112.23.121’) |
As we can see, Smart DLP allows us to create some really complex scenarios, like preventing sharing of files from folders that match the team folder path if the request is coming from outside the given IP range and the recipient is not a member of our domain.
Also, see the examples in How to secure documents with Smart DLP & CCE
Rule Violations
Smart DLP provides a way to report rule violations to admins. The main dashboard displays a widget showing current DLP statistics, including Active Downloads, Active Uploads, Active Shares, and Active Users, as well as violations. A detailed list of violations with the details of the operation that triggered each violation can be accessed in Smart DLP view for each rule.
Share Crawler
A more advanced topic worth mentioning is the Share Crawler. This process is executed on a daily basis as a part of the daily CRON and removes all shares that are blocked by the Enforcing share-related DLP rules. This removes shares that already existed when the given DLP rule was created.
Note: This operation removes those shares physically if the rule operates in the Enforcing state. This operation cannot be reverted, so admins have to be careful when using it.
In Conclusion
Smart DLP is definitely a powerful and flexible tool that can be used to provide more security and data protection to your organization. In the previous article we showed the capabilities of the metadata subsystem, which can be utilized by DLP to enforce monitoring and control over file sharing and downloads. The next article from the series will explain how the two subsystems can be linked with the Smart Classification subsystem, which allows content-based classification of files. Stay tuned.
Also, see:
Smart DLP
Intelligent Data Leak Protection – Secure Your Enterprise Content
10 Best Practices Essential for Your Data Loss Prevention (DLP) Policy

By Team FileCloud