
Many of the topics that we will cover in this new series are common sense; however, every year, we need to revamp our personal security practices in person and online. This installment will cover how we can protect our personal information throughout our day-to-day actions.
Don't Share Your Personal Information Freely
This may seem like an obvious action, but this is also one of the most common mistakes. This wasn't such a high-risk problem in the past (some 5-10 years ago). Nevertheless, we are in 2022, and your data like SSID, date of birth, full name, preferences, etc., comprise essential security access information.
For example, you may be invited to share your personal information with a store to win a prize or become eligible for a discount code. It doesn't matter if it's handwritten at a physical store or if you enter your details on an online form; submitting this kind of information is no longer an innocent thing to do. The store could share or sell your information unless you specifically opt out of this kind of third-party interaction. The store could also be the victim of a hack, in which case your information would be compromised. The best way to protect yourself is to be wary of sharing your information; anyone can use it to steal your identity, hack their way into your online accounts, or any number of unsavory tasks.
In summary, don't give out your identifying information unless you need to.
Separate your personal information from your work ID information
What does this mean? Basically, for any personal matters (online shopping, social media, communication with friends and family, etc.), use your personal information, private email, private phone, etc. For work-related communications, only use your work identity to communicate with co-workers and external contacts (vendors, customers, partners, etc.)
The objective is to separate your identities and keep them separated in every interaction.
This applies to your computer usage as well. Most internet browsers can save multiple profiles (like Google Chrome). This will help you keep your data where it belongs, so you can avoid mixing your identities and help categorize your information. Your search history, open tabs, browser extensions, and more can be saved to distinct profiles and easily accessed or updated if you have "Sync" enabled:

Creating and maintaining this separation in your mobile device can be somewhat challenging, but you can still apply the same principles and set up profiles for web browsing and apps.
Secure Your Information on Your Mobile Device
Security on mobile devices is a major topic on its own, but you can take certain steps to protect your personal information by following some simple recommendations:
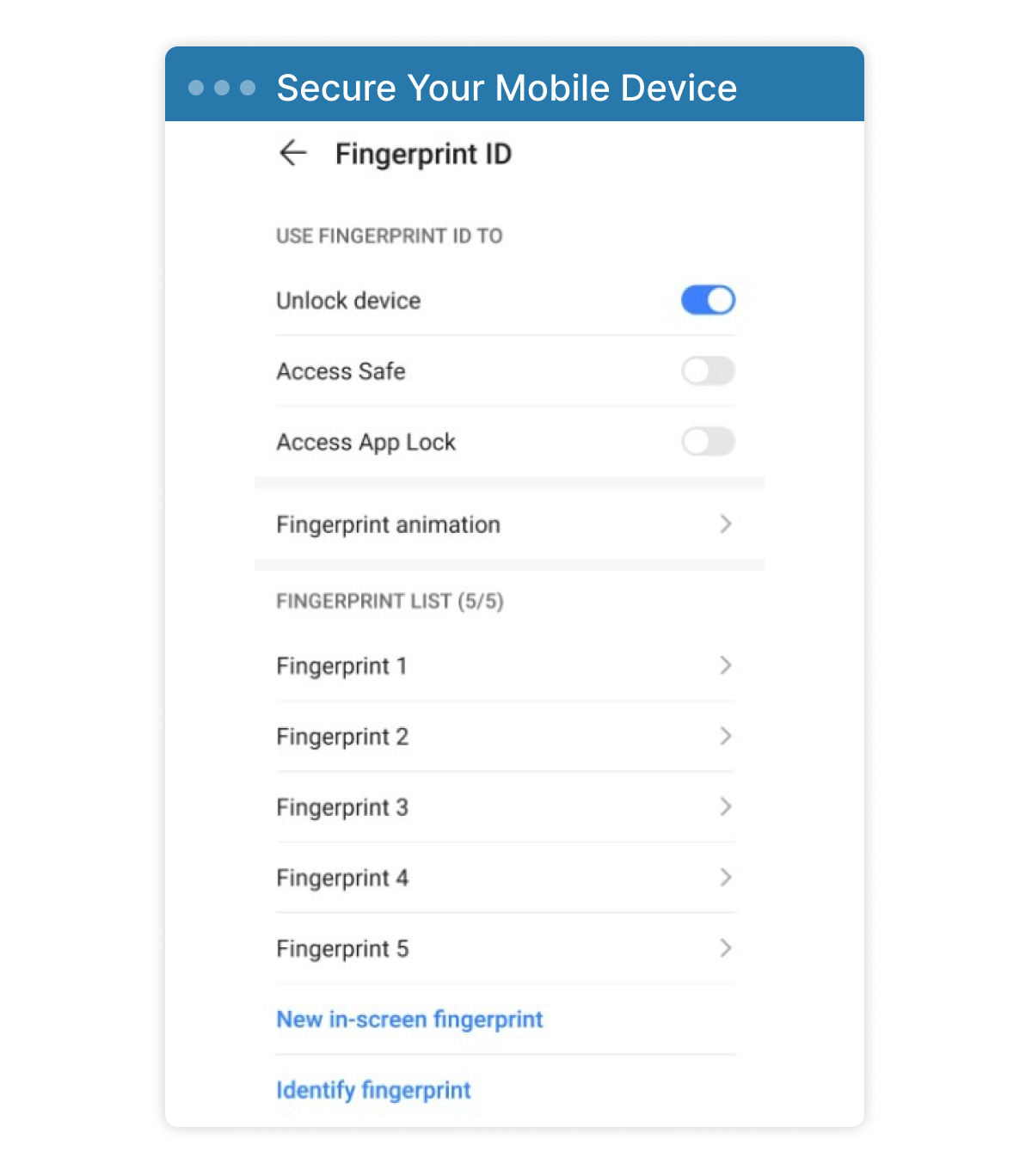
- Always enable security to unlock your phone. Even though face ID is replacing the fingerprint scanner, choose the fingerprint scanner when possible.
- Don't store important information in notes on your phone. Even though it may be practical, never store personal information on messages, pictures, notepads, or similar apps on your device. If you want to keep this information at hand, use a secure application or database for storage and access, like KeePass.
- The device and its content should be encrypted at rest. Always enable encryption, when possible, even with microSD storage. In the event of a lost phone, no one will gain access to the information stored in the device.
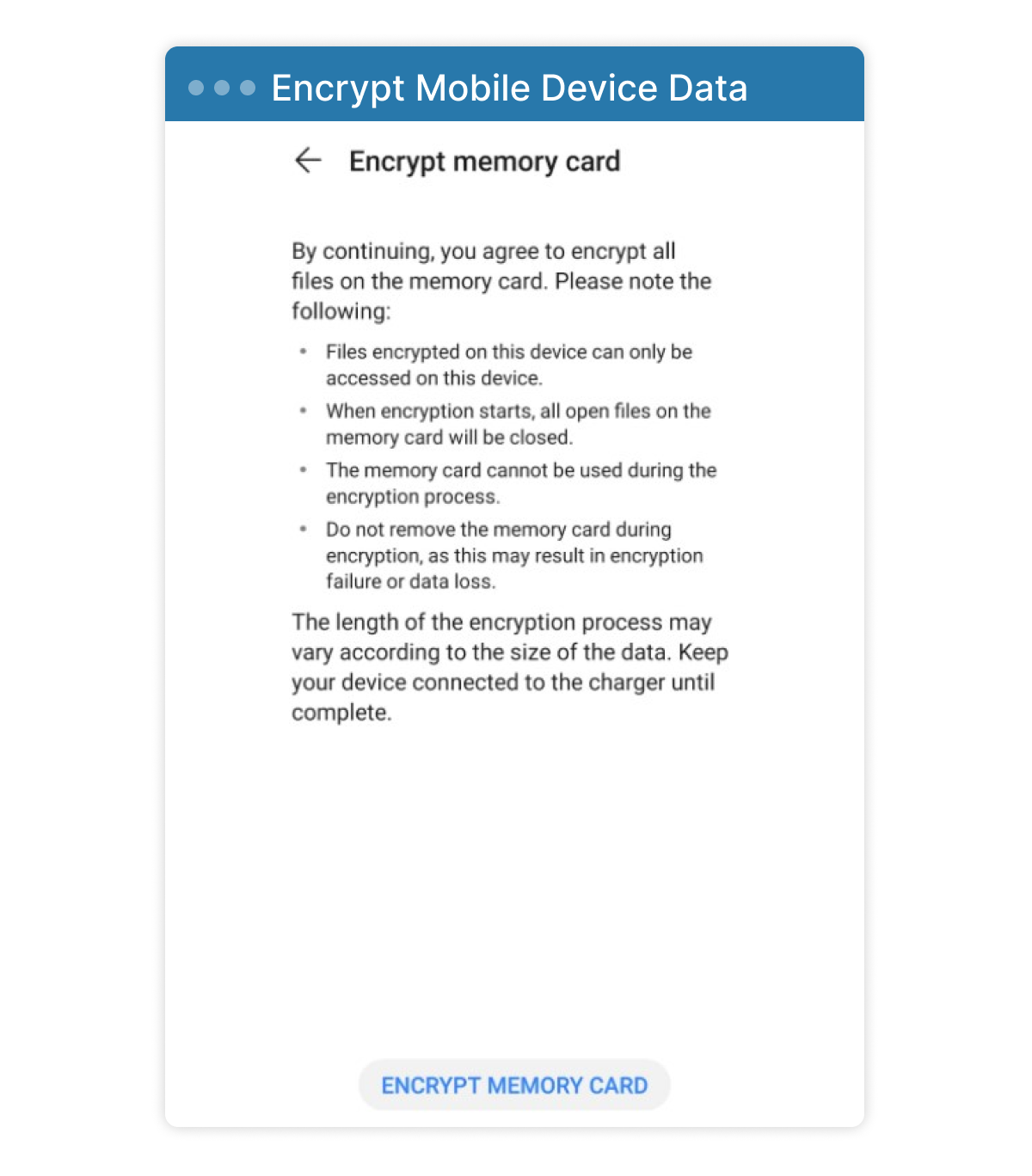
These are just basic recommendations to protect your personal information. In future articles, we will go more in-depth on encryption at rest, email communication, sharing private data securely over the internet, and other topics.
Article written by Daniel Alarcon

Product Marketing Manager