Digital Rights Management For Law Enforcement
Digital Rights Management (DRM) helps law and defense organizations who manage sensitive user information and trade secrets which they need to safeguard from unauthorized distribution. Law enforcement agencies, government and defense enterprises store their data on secure servers which are protected by separate DRM technology solutions which prevents illegal data theft or data leaks. These setups can be very costly involving private servers, DRM solution, DLP solution, VDR etc coupled together to send and receive sensitive information. FileCloud can be used as a standalone setup to include all such features at a lower cost and higher security.
Copyright and IPR Management For Law Enforcement
FileCloud DRM enables law enforcement organizations to set and impose copyright and intellectual property protection. With FileCloud’s file sharing, DRM and DLP capabilities bundle, you can store, share and protect all documents within one solution. FileCloud DRM container also supports all major file formats like Microsoft Office (Word, Powerpoint, Excel), PDF and image (jpeg, png) files. You don’t need to create separate containers for each file type, multiple file types can be included in a single secure encrypted document container within FileCloud DRM
Complete Control & Protection During Content Distribution:
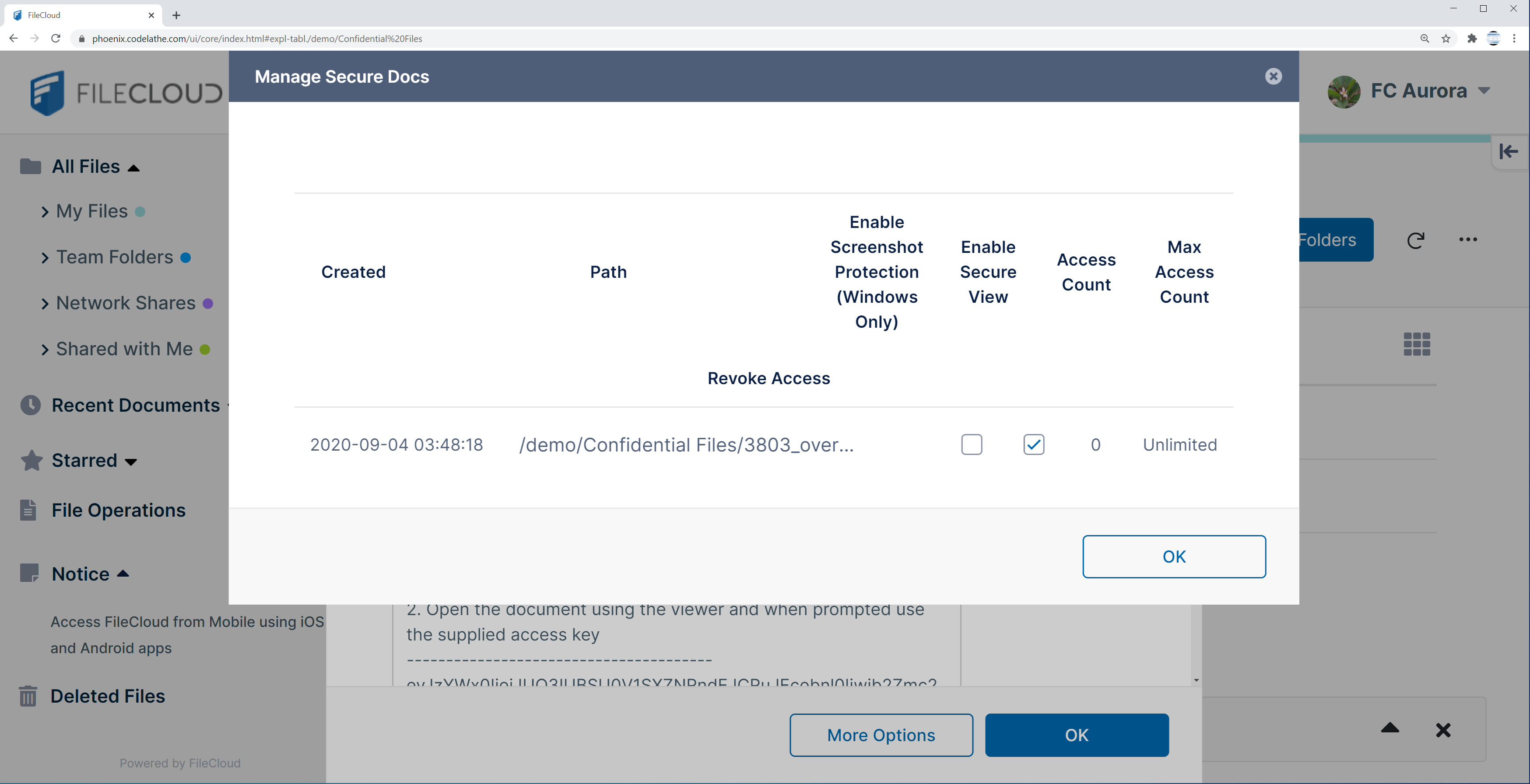
- Prevent unauthorized editing and saving of the document
- Prevent unauthorized forward and sharing of the document
- Prevent screenshots of content (part or full)
- Prevent printing of the document
- Content revocation control
- Locking document specific to some IP addresses, locations, and devices
- Watermarking on individual documents for identity
Security At Rest and During Content Distribution
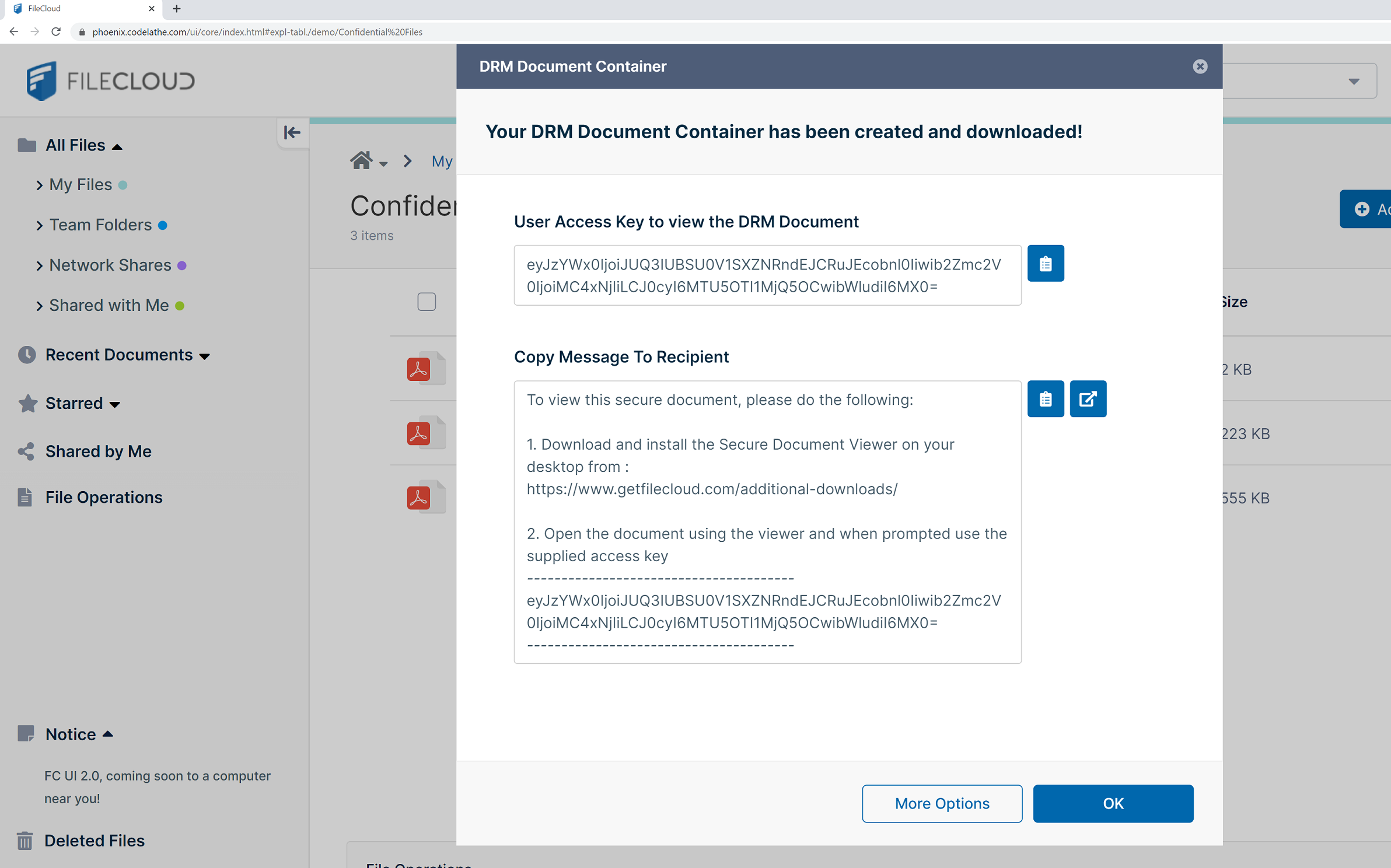
FileCloud helps track data which is shared, and helps safeguard data against data leaks. Files are protected with AES-certified 256-bit encryption at all times. File sharing can be restricted when needed, and FileCloud DRM’s secure document viewer prevents unauthorized screenshots, printing and copying of data. The encrypted document container shared externally always need an access key to access the document, which helps in accidental or intentional transmission of confidential files.